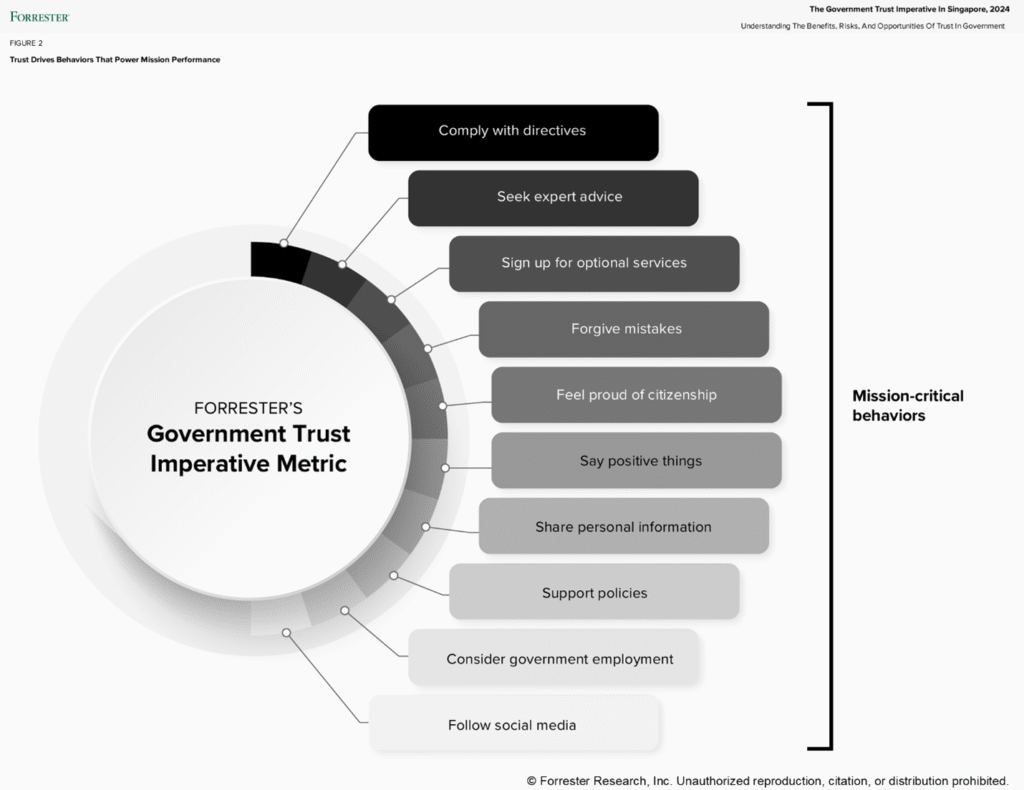
Announcing The Forrester Wave™: Security Analytics Platforms, Q2 2025 — The SIEM Vs. XDR Fight Intensifies
The Forrester Wave™: Security Analytics Platforms, Q2 2025, published today and illustrates the dramatic changes this market is undergoing as legacy security information and event management (SIEM) vendors are locked in heated competition with surging extended detection and response (XDR) providers. Over the past five months, we researched the top security analytics platforms on the market to gain a better understanding of the market landscape and identify the best product fit for our clients. This Forrester Wave evaluated 10 vendors: CrowdStrike, Elastic, Exabeam, Google, Microsoft, Palo Alto Networks, Rapid7, Securonix, Splunk, and Sumo Logic. Each vendor was evaluated on three inputs: a questionnaire for the vendors to complete, executive strategy briefings and demos, and interviews of three reference customers. The Wave included scores for 24 current-offering criteria and six strategy criteria. Read the full report here. Forrester defines security analytics platforms as: Platforms that converge data from network, identity, endpoint, application, and other security-relevant sources to generate high-fidelity behavioral alerts and facilitate rapid incident analysis, investigation, and response. This evaluation marks a turning point for the security analytics platform market. XDR vendors such as CrowdStrike and Palo Alto Networks have staked their claim for what they consider a new era of SIEM capabilities — one that is heavily focused on detection and response. The challenge with this vision is that, in contrast to many of the SIEM tools on the market, they tend to lack flexibility in data ingest, manipulation, and core compliance use cases. Some SIEMs have a longer head start, bigger communities, a wider variety of features, and an entrenched customer base. The biggest players of the industry — e.g., Google, Microsoft, and Splunk — have amassed an array of features that prioritize data, openness, and adaptability. With all of that said, customers have been frustrated with the SIEM market for a long time. Particular pain points include the quality of prebuilt analytics, the massive amounts of manual work required, and the high cost. This push and pull is leading to a shift in the market marked by the following trends: Flexibility versus specialization. Many of the veteran security analytics platforms have an understanding of data, from ingestion to manipulation and searchability. These platforms are indispensable for complex use cases that require flexibility; the trade-off is more work for the end user. Contrast that with the XDR vendors, which have limited collectors to focus on detection and response and more security-specific query languages, and they can also build out-of-the-box analytics over time. Both approaches have value — it just depends on what you want to get out of the tool. Platformization. Platformization. Platformization. Security analytics platforms (as the name suggests) are a natural fit for platformization. The security analytics platform is the central location where security operations takes place. This is why Forrester has defined it as the security analytics platform market (and not the SIEM market) since 2015. Despite efforts to deliver interoperable products with third parties, nothing integrates or bundles quite like native tools. To take advantage of the pendulum swing of platformization, some XDR vendors do not charge for the ingestion of their own endpoint detection and response (EDR) data, thereby saving practitioners money. Everyone’s favorite: Generative AI. Every vendor in this evaluation discussed its AI capabilities as part of a vision for the future. But the differentiation between vendors when it comes to AI was stark. Some vendors are pushing unique features out fast, while others are stagnating. Many vendors had some of the AI functionality we have come to expect: incident summaries, chatbots, and query language translation. The vendors that differentiated, however, delivered AI agents, automated parsing, and other leading features. AI will change the way security operations functions, and betting on the right horse now will enable your team to change with it. For a deeper look into the market, Forrester clients can read the full report, The Forrester Wave™: Security Analytics Platforms, Q2 2025. Check out the results for all 10 vendors, including the specific criteria that differentiated them and why. If you have any questions about the changes happening in the security analytics platform market, book an inquiry or guidance session with me. source